The first Logic Apps SDK for .NET (v0.1.0) was released on August 28. Stephen Siciliano covered it in the LogicAppsIO Community WebCast on August 27.
But there haven’t been many blog posts on how to use it, nor many samples. So here we go: How to use the SDK.
Step 1: Download and install the SDK.
Luckily, this is really simple with NuGet. You can find the NuGet page for the SDK here: https://www.nuget.org/packages/Microsoft.Azure.Management.Logic.
As per the instructions on the page, you can install it using the NuGet Package Manager Console in Visual Studio by using this on the command line: Install-Package
Microsoft.Azure.Management.Logic -Pre.
This will install the SDK and all the pre-reqs in the packages subfolder of your project.
Step 2: Write some code to use it.
This was a bit harder. I started off thinking I’d copy the code from the WebCast,the code that Stephen showed https://www.youtube.com/watch?v=N-ZDaKsH6BY
If you look at the WebCast, and pause it, you can see this on screen:
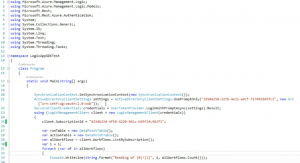
Note that the first thing we have to do is get some credentials – in fact, the call on line 22 (UserTokenProvider.LoginWithPromptAsync) will pop up the usual Azure Login window (where you can log in with an Org ID or MS Account), or it will skip it if the cached token is still valid form the last login attempt.
However, a number of classes in the above code don’t exist in the any of the assemblies installed with the Logic Apps SDK – specifically the ServiceClientCredentials and UserTokenProvider.
I eventually found them referenced in the source code for the AutoREST tool on github: https://github.com/matt-gibbs/AutoRest/tree/master/ClientRuntimes/CSharp/ClientRuntime.Azure.Authentication
The reason they’re not in the SDK is that these classes are defined in the Microsoft.Rest.ClientRuntime.Azure.Authentication.dll assembly, which is supplied with the SDK – but the SDK comes with v0.9.1 of this assembly whereas these classes weren’t added till v0.9.3 of the assembly.
There is a NuGet page for v0.9.3 but it indicates that v0.9.3 has been withdrawn: https://packages.nuget.org/packages/Microsoft.Rest.ClientRuntime.Azure.Authentication/0.9.3 (You can actually install v0.9.3 from the NuGet package manager, but you get an assembly manifest mismatch exception when you try and use it. I suspect Microsoft are still working on v0.9.3.)
In the meantime, there is a solution – you don’t actually need v0.9.3 to use the SDK: by looking at the source code for these new classes, I saw that they were just a wrapper for some common code that we’ve been using to access Azure SDKs for some time now.
So here we go:
Step 3: How to prompt for credentials to use with the SDK.
Basically, in order to get the credentials to use with the SDK, we need to use this code:
///
/// Displays the Azure login window, prompts the user to login,
/// and returns a
TokenCredentials
“/> instance for the logged-in user.
/// >
/// tenant“>AD
Tenant to use – if not supplied, common tenant is used.>
///
TokenCredentials
“/> instance.>
private static TokenCredentials GetAuthorizationToken(string tenant
= “common”)
{
string tokenAudience
= “https://management.core.windows.net/”;
string clientRedirectUri
= “urn:ietf:wg:oauth:2.0:oob”;
string clientId
= “1950a258-227b-4e31-a9cf-717495945fc2”;
string enableMagicCookie
= “site_id=501358&display=popup”;
AuthenticationContext context
= new AuthenticationContext(string.Format(“https://login.windows.net/{0}”,
tenant),
true, TokenCache.DefaultShared);
AuthenticationResult result
= context.AcquireToken(
tokenAudience,
clientId,
new Uri(clientRedirectUri),
PromptBehavior.Always,
UserIdentifier.AnyUser,
enableMagicCookie);
var newUserId
= new UserIdentifier(result.UserInfo.DisplayableId,
UserIdentifierType.RequiredDisplayableId);
return new TokenCredentials(result.CreateAuthorizationHeader().Substring(“Bearer
“.Length));
}
This code will bring up the standard Azure Credential prompt window, and return a TokenCredentials instance, which can be used with the SDK.
Note: you may notice some hard-coded value sin there and be wondering what they are.
We’re using Azure AD to do the login – and Azure AD wants to know what Tenant to use, and what client is trying to access AD. For your own applications, you can set all this up in your own Azure AD, but in our case we don’t yet know which Tenant to use, and we want to use a common client ID.
So we use the common tenant, and the clientId we’re using identifies us as PowerShell (you’ll see a lot of demos using the same clientId, as it’s the easiest one to use to access Azure).
So your code to get, say, a list of Workflow names will look like this:
var credentials = GetAuthorizationToken();
using (LogicManagementClient client
= new LogicManagementClient(credentials))
{
client.SubscriptionId = “
”
;
PageWorkflow>
workflows = client.Workflows.ListBySubscription();
foreach (Workflow wf in workflows)
{
Console.WriteLine(wf.Name);
}
}
The Using statements you’ll need are:
using System; using Microsoft.Azure.Management.Logic; using Microsoft.Azure.Management.Logic.Models; using Microsoft.Rest; using Microsoft.Rest.Azure; using Microsoft.IdentityModel.Clients.ActiveDirectory;
Note: you’ll need to get your subscription ID and put it in the code above where it says “
”
And that’s it.
Now you can start exploring all the methods and properties exposed by the SDK.
Bear in mind that the SDK just wraps up calls made to the Azure Resource Manager via REST – there’s no magic here.
The full class looks like this:
using System;
using Microsoft.Azure.Management.Logic;
using Microsoft.Azure.Management.Logic.Models;
using Microsoft.Rest;
using Microsoft.Rest.Azure;
using Microsoft.IdentityModel.Clients.ActiveDirectory;
namespace TestLogicAppsSDK
{
class Program
{
static void Main(string[]
args)
{
var credentials
= GetAuthorizationToken();
//SynchronizationContext.SetSynchronizationContext(new
SynchronizationContext());
//ActiveDirectoryClientSettings settings
= ActiveDirectoryClientSettings.UsePromptOnly(“1950a258-227b-4e31-a9cf-717495945fc2”,
new Uri(“urn:ietf:wg:oauth:2.0:oob”));
//ServiceClientCredentials credentials
= UserTokenProvider.LoginWithPromptAsync(settings).Result;
using (LogicManagementClient client
= new LogicManagementClient(credentials))
{
client.SubscriptionId = “3d50ae08-501b-4414-97ef-d2eee1c36beb”;
PageWorkflow>
workflows = client.Workflows.ListBySubscription();
foreach (Workflow wf in workflows)
{
Console.WriteLine(wf.Name);
}
}
}
///
/// Displays
the Azure login window, prompts the user to login,
/// and returns
a
TokenCredentials
“/> instance for the logged-in
user.
/// >
/// tenant“>AD
Tenant to use – if not supplied, common tenant is used.>
///
TokenCredentials
“/> instance.>
private static TokenCredentials GetAuthorizationToken(string tenant
= “common”)
{
string tokenAudience
= “https://management.core.windows.net/”;
string clientRedirectUri
= “urn:ietf:wg:oauth:2.0:oob”;
string clientId
= “1950a258-227b-4e31-a9cf-717495945fc2”;
string enableMagicCookie
= “site_id=501358&display=popup”;
AuthenticationContext context
= new AuthenticationContext(string.Format(“https://login.windows.net/{0}”,
tenant),
true, TokenCache.DefaultShared);
AuthenticationResult result
= context.AcquireToken(
tokenAudience,
clientId,
new Uri(clientRedirectUri),
PromptBehavior.Always,
UserIdentifier.AnyUser,
enableMagicCookie);
var newUserId
= new UserIdentifier(result.UserInfo.DisplayableId,
UserIdentifierType.RequiredDisplayableId);
return new TokenCredentials(result.CreateAuthorizationHeader().Substring(“Bearer
“.Length));
}
}
}
Here’s a full copy of the source code, with the packages and all: http://www.bizbert.com/bizbert/content/binary/TestLogicAppsSDK.zip”>TestLogicAppsSDK.zip
(2.5 MB)